TagCyber just released an ROI study on the Reach Platform.
Read their findingsTrusted by leading security teams





Success Stories
Discover how organizations like yours are closing security gaps, maximizing their tools, and reducing complexity with Reach - a unified platform with AI agents to help teams improve posture and performance. These are their stories.
Use Cases
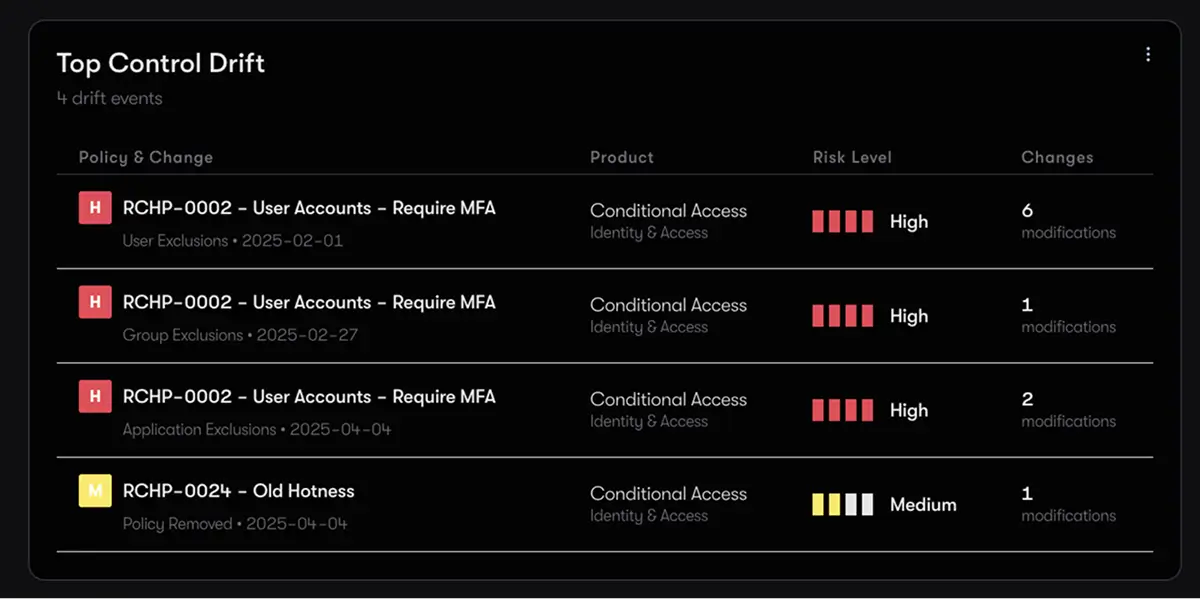
Reach ConfigIQ Drift™ detects drift the moment it happens, helping you stay aligned to policy, prevent regressions, and fix issues before they become exposure.
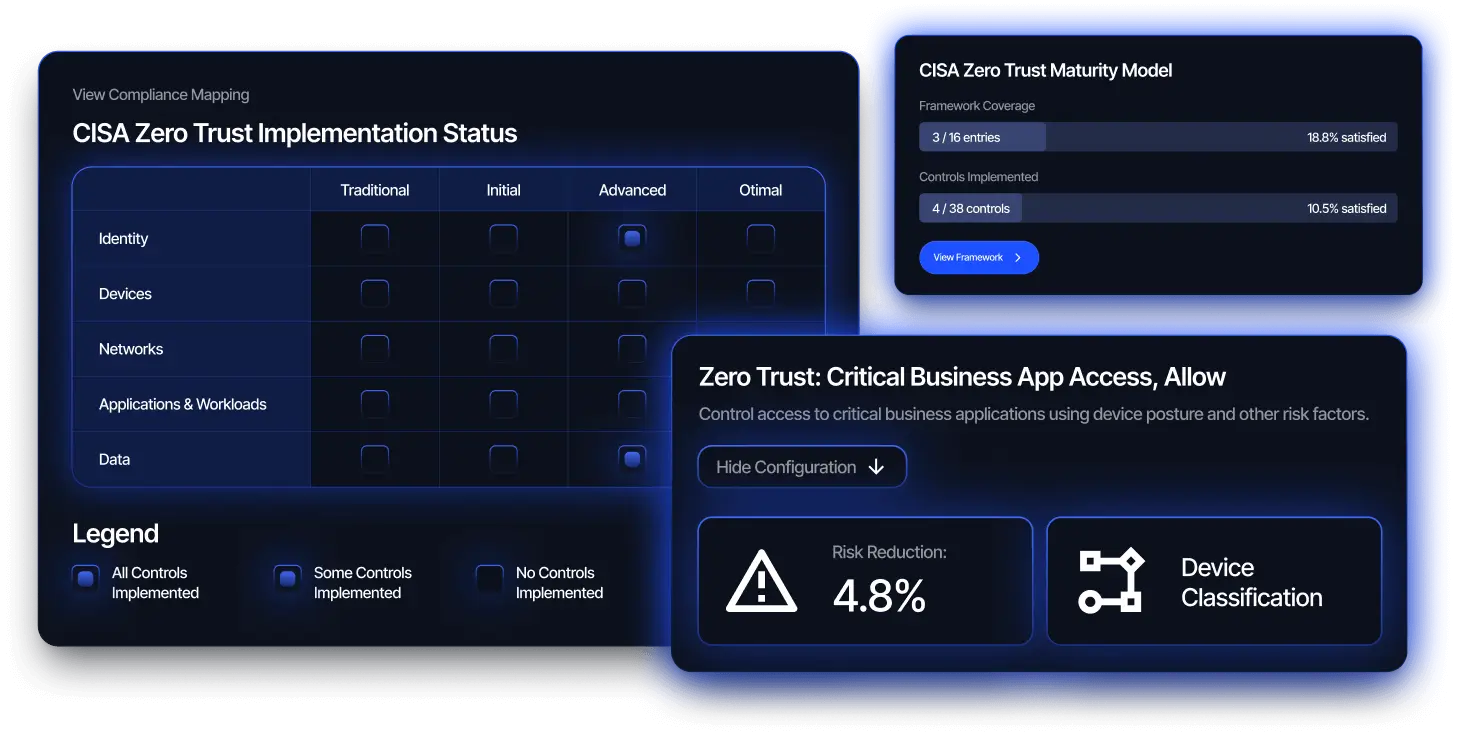
Reach leverages analytics, automation and an understanding of risk exposure to mature your Zero Trust Posture.
AI Is already inside, and Reach helps you ensure safe use across your organization.


Reach Integrations
Reach integrates seamlessly with your identity, endpoint protection, email security, and network security tools to find and fix hidden risks. With integrations into ticketing systems, Reach also helps you deploy configuration updates directly to your tools, turning insights into action and closing gaps quickly.
Why it matters
Reach helps you get the most from your existing security stack by uncovering exposure, misconfigurations, and weaknesses that tools often miss. Using AI agents, it prioritizes and drives remediation based on real exposure, reducing operational costs and enabling measurable, preventive action, all from the leader in AI-Native Exposure Management.
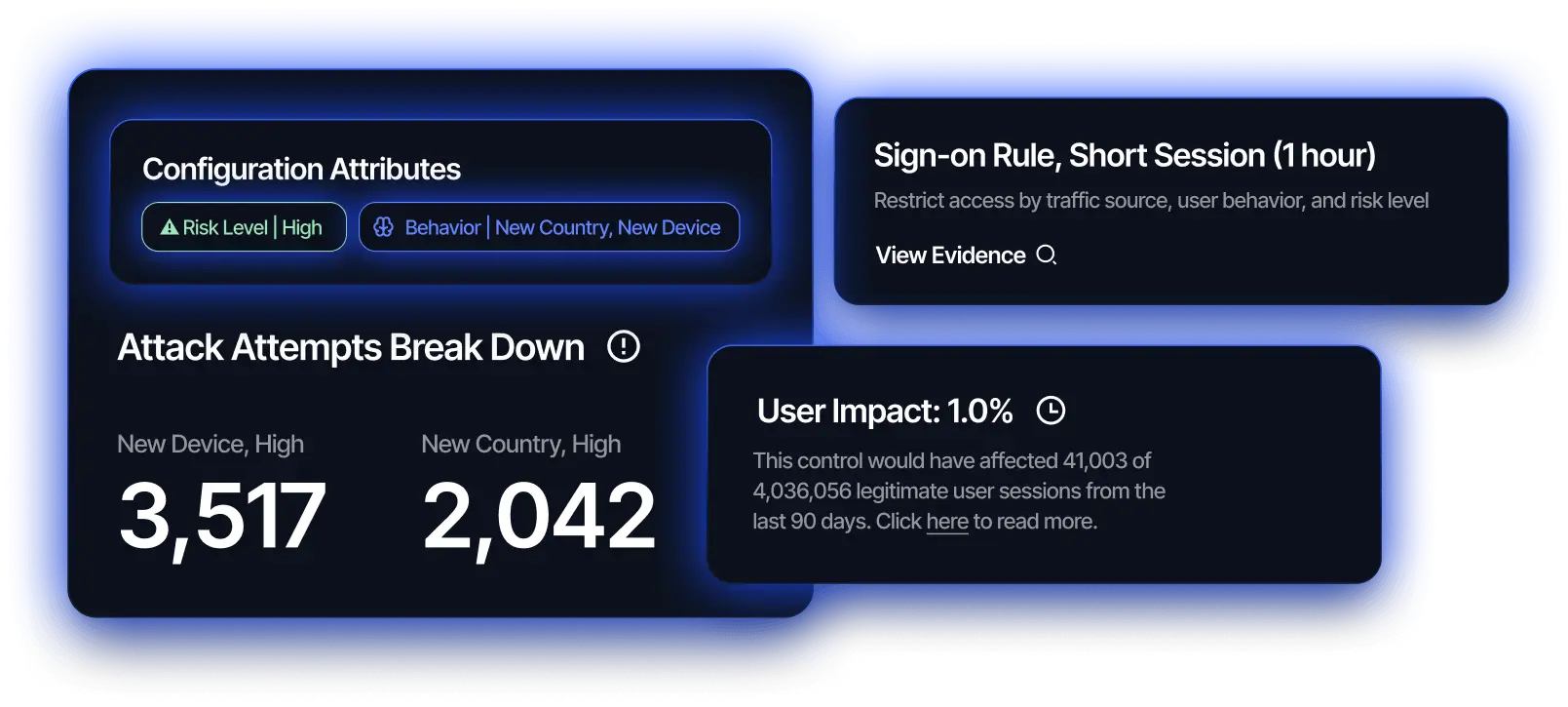
Reach identifies exposure that is actually reachable, like those on end-user devices that enable ransomware delivery. By focusing on real exposure, it helps you prioritize actions that measurably reduce risk.
Weak controls create protection gaps like those that allow session hijacking or lateral movement. Reach helps you strengthen your posture by continuously validating whether your security controls are working as intended.
Misconfigurations leave systems open to attack. Reach finds these weaknesses across your stack and recommends precise, context-aware fixes that simplify remediation and reduce friction for your team.
Spotlight on Success
Watch how customers are using Agentic AI from Reach to operate their infrastructure.
Reach connects directly to your existing identity, endpoint protection, email, and network security tools to show how effectively they’re deployed and configured. By analyzing millions of data points across your environment, Reach uncovers misconfigured, underused, or incomplete controls that create hidden exposure across people, assets, and systems.
Reach maps risks to the ever-changing threats your organization faces, analyzing reachability, configurability, and attacker behavior to surface the most impactful changes. This helps you focus on what truly reduces risk and improves the return on your current security investments.
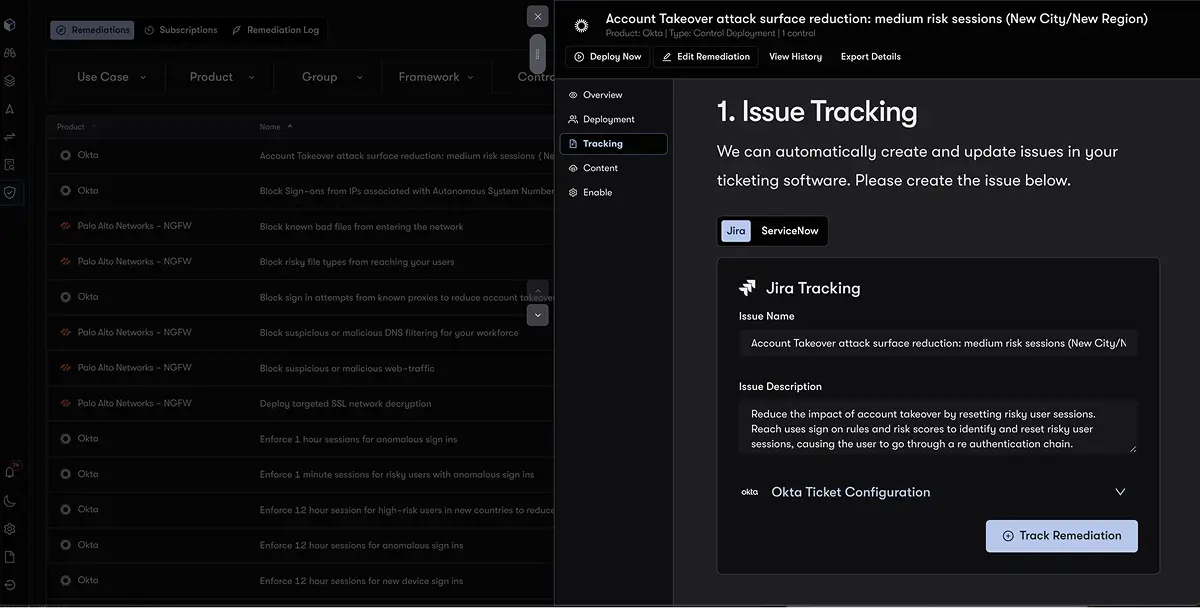
Reach translates insights into action with detailed configuration guides, automated workflows, and direct integration with your ticketing systems,including ServiceNow and Jira. Your team can quickly deploy changes and close gaps without adding friction to existing processes.
Security posture isn’t static. Reach continuously monitors your configurations to detect drift, validate that controls are working as intended, and ensure your defenses stay aligned with your evolving environment and threat landscape. AI agents help you stay ahead of change, ensuring posture is maintained, not just assessed.
Unlock the full power of your security stack with a free tool rationalization assessment.
Read-only API key for a security tool of your choice
Create your account and setup the integration
Get results across licensing, control mapping, risk exposure, and posture